SSO/Office365: Difference between revisions
Appearance
m Redigeret tekst og tilføjet FAQ |
No edit summary |
||
| Line 49: | Line 49: | ||
****The '''LocalCertificateFile''' must be entered with a PFX certificate. This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) | ****The '''LocalCertificateFile''' must be entered with a PFX certificate. This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) | ||
****The '''LocalCertificatePassword''' must be entered to be able to read the PFX certificate | ****The '''LocalCertificatePassword''' must be entered to be able to read the PFX certificate | ||
****The '''PartnerCertificateFile''' is a certificate the is generated during Azure SSO setup (The file downloaded from '''Certificate (Base64)'''). | ****The '''PartnerCertificateFile''' is a certificate the is generated during Azure SSO setup (The file downloaded from '''Certificate (Base64)'''). Remember to include the filename extension | ||
**** | *****This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) | ||
****Click '''Save''' | ****Click '''Save''' | ||
***Click '''Enable''' | ***Click '''Enable''' | ||
| Line 80: | Line 80: | ||
*Select it and click '''Add''' | *Select it and click '''Add''' | ||
== FAQ : == | ==FAQ :== | ||
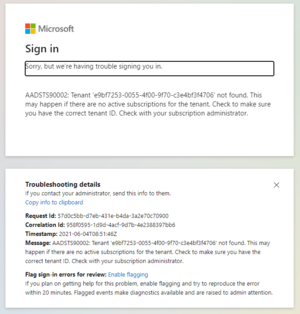
If you get this message when trying to connect it might be a matter of waiting for Client tenant distribution | If you get this message when trying to connect it might be a matter of waiting for Client tenant distribution | ||
[[File:SSO login error message.png|left|thumb]] | [[File:SSO login error message.png|left|thumb]] | ||
Revision as of 09:00, 4 June 2021
How to use Office 365 as login provider instead of Active Directory
You need to create an Enterprise application
Login into portal.azure.com
- Find Azure Active Directory
- Find Enterprise applications
- Click New application
- Click Create your own application
- Enter a name
- Choose Integrate any other application you don't find in the gallery (Non-gallery)
- Click Create (This will also create an App registration)
- Find Properties for the Enterprise application you just created
- Set User assignment required? and Visible to users? to false
- Click Save
- Click Single sign-on
- Click SAML
- Click edit under Basic SAML Configuration
- Enter this in Identifier (Entity ID)
- Enter the URL https://{URL}/{CustomerID} replace {CustomerID} with you number. This can be found in the configurator program under license info
- Delete other URL's
- Enter this in Reply URL (Assertion Consumer Service URL)
- https://{URL}/SSO/AssertionConsumerServiceAzureAd.aspx
- Enter this in Identifier (Entity ID)
- Under SAML Signing Certificate
- Click download for Certificate (Base64)
- This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot)
- Click edit under Basic SAML Configuration
- Find Azure Active Directory
- Find App registrations
- Find your application that was created as an Enterprise applications
- Click API permissions
- Click Add a permission
- Click Microsoft Graph
- Click Application permissions
- Add these permissions
- User.ReadWrite.All
- UserAuthenticationMethod.ReadWrite.All
- Add these permissions
- Click Application permissions
- Click Microsoft Graph
- Click Grant admin consent for {Tenant}
- Click Yes
- Open SQL Management Studio connect to the database
- Run this SQL Command
- Update UMSWebGeneralSettings Set SetSSO = 1
- Run this SQL Command
- Open UMS web
- You will be redirected to SSO setup
- Click Add, enter a name and click Create
- Choose the name in the drop down and click Edit
- Click Add under the section Create new Single Sign On
- Choose Azure AD in the Type drop down
- In the boxes Name, SingleSignOnServiceUrl and SingleLogoutServiceUrl replace {appId} with the application id of your Enterprise application
- The LocalCertificateFile must be entered with a PFX certificate. This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot)
- The LocalCertificatePassword must be entered to be able to read the PFX certificate
- The PartnerCertificateFile is a certificate the is generated during Azure SSO setup (The file downloaded from Certificate (Base64)). Remember to include the filename extension
- This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot)
- Click Save
- Click Enable
- Click Save
- Click Add to website
- Choose website setting and click Add
- You will be redirected to SSO setup
- Open UMS Configurator program
- Click Web Setup
- Select General settings
- Select Azure AD in the Check login against drop down list
- Open SQL Management Studio on the UMS Server and connect to the database
- Run this SQL Command
- Update UMSWebGeneralSettings Set SetSSO = 0
- Run this SQL Command
- Restart IIS
- The changes above may take some time to be distributed into Client Tenant system
Reset password for others
- Go to Azure Active Directory
- Click Roles and administrators
- Find Password administrator
- Click Add assignments
- Find the name of the Enterprise application you created earlier
- Select it and click Add
FAQ :
If you get this message when trying to connect it might be a matter of waiting for Client tenant distribution