SSO/Office365: Difference between revisions
No edit summary |
|||
| (2 intermediate revisions by one other user not shown) | |||
| Line 26: | Line 26: | ||
***Enter this in '''Reply URL (Assertion Consumer Service URL)''' | ***Enter this in '''Reply URL (Assertion Consumer Service URL)''' | ||
****'''<nowiki>https://{URL}/SSO/AssertionConsumerServiceAzureAd.aspx</nowiki>''' | ****'''<nowiki>https://{URL}/SSO/AssertionConsumerServiceAzureAd.aspx</nowiki>''' | ||
**Under '''Attributes & Claims''' | |||
***Only keep "'''Unique User Identifier'''" with the value "'''user.localuserprincipalname'''" | |||
**Under '''SAML Signing Certificate''' | **Under '''SAML Signing Certificate''' | ||
***Click download for '''Certificate (RAW)''' | ***Click download for '''Certificate (RAW)''' | ||
***This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) | ***This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) | ||
*Open '''SQL Management Studio''' connect to the database | *Open '''SQL Management Studio''' connect to the database | ||
**Run this SQL Command | **Run this SQL Command | ||
| Line 50: | Line 40: | ||
**Choose the name in the drop down and click '''Edit''' | **Choose the name in the drop down and click '''Edit''' | ||
**Click '''Add''' under the section '''Create new Single Sign On''' | **Click '''Add''' under the section '''Create new Single Sign On''' | ||
***Choose '''Azure AD''' in the '''Type''' drop down | ***Choose '''Azure AD''' in the '''Type''' drop down | ||
*** | ***in the boxes | ||
****'''Name''' | |||
****'''SingleSignOnServiceUrl''' | |||
***The '''LocalCertificatePassword''' must be entered to be able to read the PFX certificate | ****'''SingleLogoutServiceUrl''' | ||
***The '''PartnerCertificateFile''' is a certificate the is generated during Azure SSO setup (The file downloaded from '''Certificate (Raw)'''). Remember to include the filename extension | ***replace '''{TenantID}''' with the application id of your Enterprise application | ||
****This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) | **The '''LocalCertificateFile''' must be entered with a PFX certificate. This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) - THIS MUST '''NOT''' BE THE WEB COMMUNICATION CERTIFICATE, please use a different certificate. | ||
***Click '''Save''' | *** '''see [https://wiki.inlogic.dk/index.php/SSO_UMS#Open_AD_FS_Management_on_the_primary_ADFS_Server. SSO UMS] for more information about creating certificates and UMS SSO configuration (This is needed to create the selfsigned certificate)''' | ||
****The '''LocalCertificatePassword''' must be entered to be able to read the PFX certificate | |||
****The '''PartnerCertificateFile''' is a certificate the is generated during Azure SSO setup (The file downloaded from '''Certificate (Raw)'''). Remember to include the filename extension | |||
*****This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) | |||
****Click '''Save''' | |||
**Click '''Enable''' | **Click '''Enable''' | ||
**Click '''Save''' | **Click '''Save''' | ||
| Line 95: | Line 89: | ||
==FAQ :== | ==FAQ :== | ||
If you get this message when trying to connect it might be a matter of waiting for Client tenant distribution | If you get this message when trying to connect it might be a matter of waiting for Client tenant distribution | ||
[[File: | [[File:SSO_login_error_message.png|none|frame]] | ||
=== Cross-origin token redemption is permitted only for the 'Single-Page Application' === | === Cross-origin token redemption is permitted only for the 'Single-Page Application' === | ||
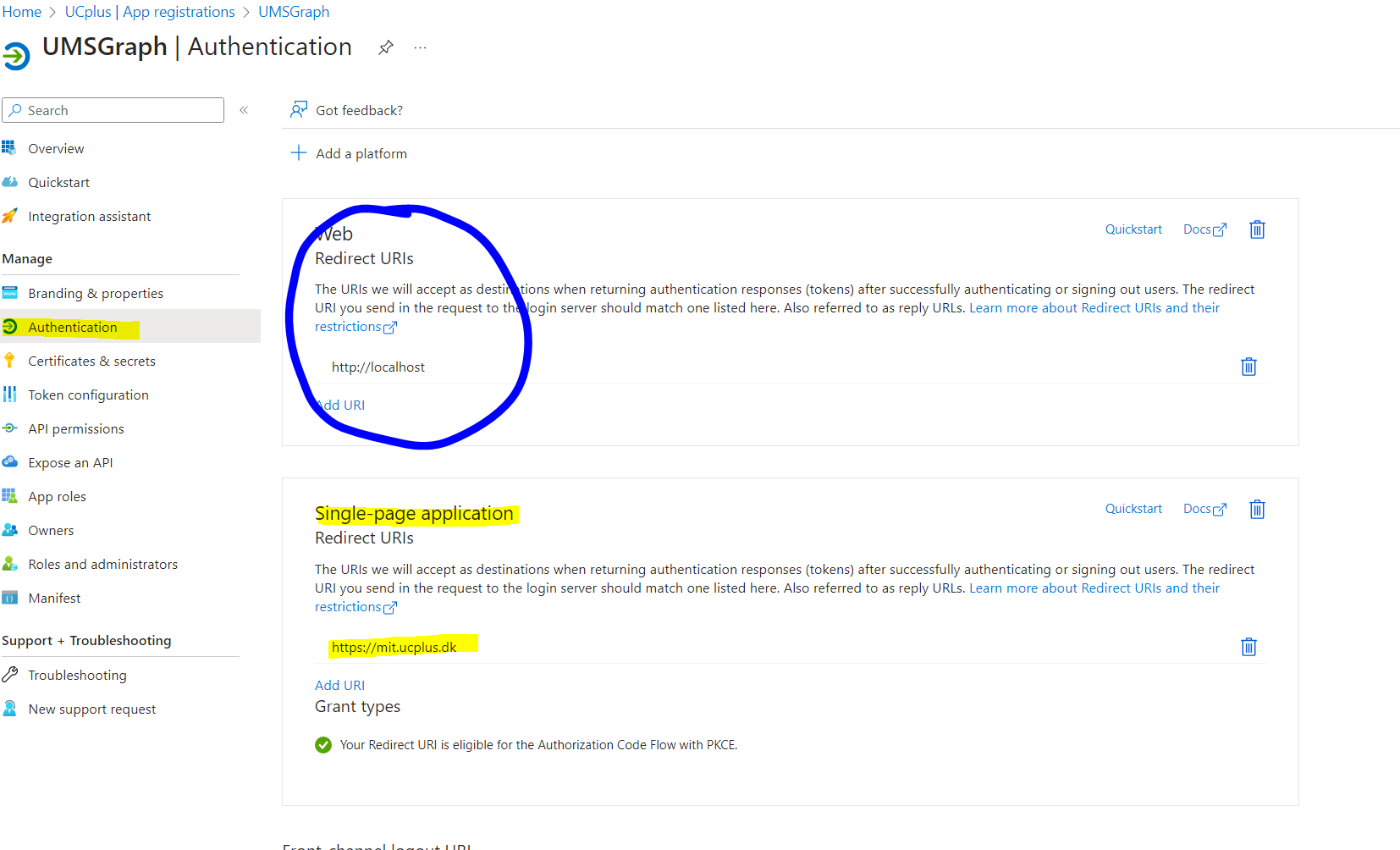
If this error occurs, this is most likely the authentication settings on the UMS App registration. Web should be filled out with localhost as the image below displays and the Single-page application should be your UMS Web URL. | If this error occurs, this is most likely the authentication settings on the UMS App registration. Web should be filled out with localhost as the image below displays and the Single-page application should be your UMS Web URL. | ||
In most cases this would be something like <nowiki>https://ums.enterschoolnamehere.dk</nowiki>.[[File:Azure_App_Registration_Authentication.png|none| | In most cases this would be something like <nowiki>https://ums.enterschoolnamehere.dk</nowiki>.[[File:Azure_App_Registration_Authentication.png|none|frame]] | ||
Latest revision as of 09:22, 31 October 2025
This feature requires the SSO module included in License
You also need Office365 Tenant settings to be setup in configurator (Must be same tenant as users are synced with)
How to use Office 365 as login provider instead of Active Directory
You need to create an Enterprise application
Login into portal.azure.com
- Find Azure Active Directory
- Find Enterprise applications
- Click New application
- Click Create your own application
- Enter a name
- Choose Integrate any other application you don't find in the gallery (Non-gallery)
- Click Create (This will also create an App registration)
- Find Properties for the Enterprise application you just created
- Set User assignment required? and Visible to users? to false
- Click Save
- Click Single sign-on
- Click SAML
- Click edit under Basic SAML Configuration
- Enter this in Identifier (Entity ID)
- Enter the URL https://{URL}/{CustomerID} replace {CustomerID} with you number. This can be found in the configurator program under license info
- Delete other URL's
- Enter this in Reply URL (Assertion Consumer Service URL)
- https://{URL}/SSO/AssertionConsumerServiceAzureAd.aspx
- Enter this in Identifier (Entity ID)
- Under Attributes & Claims
- Only keep "Unique User Identifier" with the value "user.localuserprincipalname"
- Under SAML Signing Certificate
- Click download for Certificate (RAW)
- This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot)
- Click edit under Basic SAML Configuration
- Open SQL Management Studio connect to the database
- Run this SQL Command
- Update UMSWebGeneralSettings Set SetSSO = 1
- Run this SQL Command
- Open UMS
- You will be redirected to SSO setup
- Click Add, enter a name and click Create
- Choose the name in the drop down and click Edit
- Click Add under the section Create new Single Sign On
- Choose Azure AD in the Type drop down
- in the boxes
- Name
- SingleSignOnServiceUrl
- SingleLogoutServiceUrl
- replace {TenantID} with the application id of your Enterprise application
- The LocalCertificateFile must be entered with a PFX certificate. This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot) - THIS MUST NOT BE THE WEB COMMUNICATION CERTIFICATE, please use a different certificate.
- see SSO UMS for more information about creating certificates and UMS SSO configuration (This is needed to create the selfsigned certificate)
- The LocalCertificatePassword must be entered to be able to read the PFX certificate
- The PartnerCertificateFile is a certificate the is generated during Azure SSO setup (The file downloaded from Certificate (Raw)). Remember to include the filename extension
- This file must be placed in the root directory of your UMS Academic installation (Normally C:\inetpub\wwwroot)
- Click Save
- see SSO UMS for more information about creating certificates and UMS SSO configuration (This is needed to create the selfsigned certificate)
- Click Enable
- Click Save
- Click Add to website
- Choose website setting and click Add
- Open UMS Configurator program
- Click Web Setup
- Select General settings
- Select Azure AD in the Check login against drop down list
- Open SQL Management Studio on the UMS Server and connect to the database
- Run this SQL Command
- Update UMSWebGeneralSettings Set SetSSO = 0
- Run this SQL Command
- Restart IIS
- The changes above may take some time to be distributed into Client Tenant system
Reset password for others
- Go to Azure Active Directory
- Click Roles and administrators
- Find Password administrator
- Click Add assignments
- Find the name or ObjectID of the APP Registration entered into your Office365 tenant settings.
- Select it and click Add
Change own password VIA UMS Website
See also Password Change Azure AD
Notice when using "Check Login in Azure AD" in Web Setup
In order to work the user-domain needs to be configured in both Office365 Tenant-settings and User-settings.
FAQ :
If you get this message when trying to connect it might be a matter of waiting for Client tenant distribution
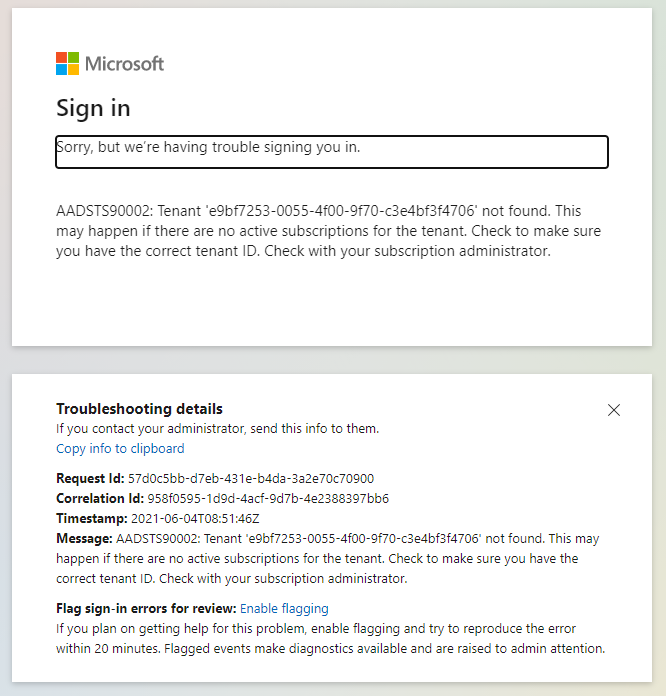
Cross-origin token redemption is permitted only for the 'Single-Page Application'
If this error occurs, this is most likely the authentication settings on the UMS App registration. Web should be filled out with localhost as the image below displays and the Single-page application should be your UMS Web URL.
In most cases this would be something like https://ums.enterschoolnamehere.dk.